Throughout my career working in digital security, I have been engaged in many smaller and sometimes larger research projects. This page includes a selection of these projects. (Before working in digital security, I worked as a junior researcher in pure mathematics, a job which obviously included a large research component.)
Silent Push
I have been working for Silent Push, a security start-up, in 2021 and 2022 and again from 2024. As a senior threat analyst I am part of the threat research team, which publishes reports and generates feeds for customers. My particular focus is on APTs.
We do sometimes publish blog posts. Here is a sample of research I have been particularly involved in:
- Salt Typhoon and UNC4841: Silent Push Discovers New Domains; Urges Defenders to Check Telemetry and Log Data (September 2025)
- Smishing Triad: Chinese eCrime Group Targets 121+ Countries, Intros New Banking Phishing Kit (April 2025)
- Silent Push tracks threat actor targeting UK banks in ongoing AnyDesk social engineering campaign (August 2024)
- More LodaRAT Infrastructure Targeting Bangladesh Uncovered (2021)
- IcedID Command and Control Infrastructure (2021)
Twitter botnet takedown
In 2013, I discovered some accounts on Twitter that were sending identical tweets. Studying these tweets and then writing a tool that detected similar ones helped me find more than 45,000 fake Twitter accounts that were being sold as followers. Twitter removed the accounts after I reported them. A brief write-up appeared on Virus Bulletin’s blog.
Spam: quality vs quantity
For more then ten years while working at Virus Bulletin, I researched unwanted and malicious email campaigns and products’ ability to block them. The most important trend I noticed during this time, was that the more successful campaigns gradually became less prolific but at the same time did a better job at evading filters.
In security, we are often impressed by big numbers, but even in something as mundane as email spam, size doesn’t always matter: a campaign sending 25,000 emails can be more effective than one sending many millions. Here are two examples of this kind of research, a more concluding version was presented at Botconf 2020.
Mevade (Sefnit) botnet
In 2013, together with João Gouveia from Anubisnetworks, I looked into network traffic of what appeared to be a mysterious but prolific botnet. We were able to link it to Mevade (also known as Sefnit), a botnet used to mine for cryptocurrencies. We presented our research at Botconf 2014 in Nancy and also did a write-up for Anubisnetworks’ blog (of which only an archived version exists).
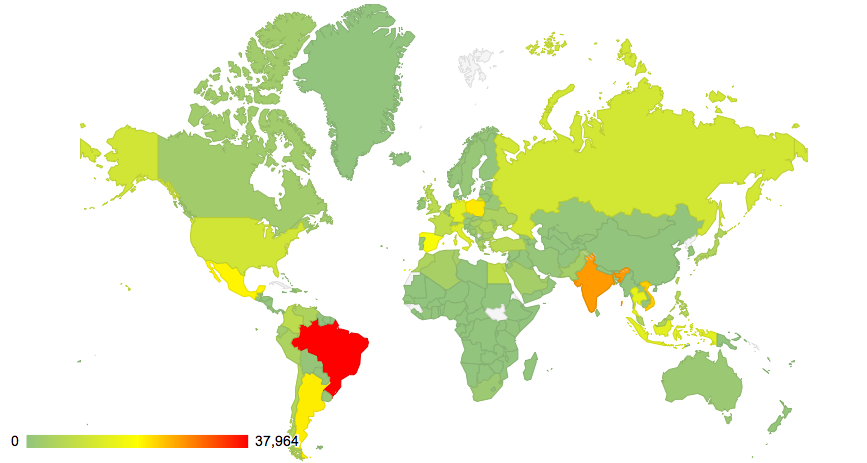
Qakbot botnet
In 2014, João looked at the network traffic of another botnet, Qakbot (also known as Qbot and Pinkslipbot). Seven years later, Qakbot continues to be active and has been the initial infection for a number of prominent ransomware cases. An archived version of the blog post we wrote still exists.
Dridex malicious spam campaign
This is an example of some ad hoc malware analysis performed with two colleagues at Virus Bulletin, resulting in a short blog post.
Phone support scams
During the early days of phone support scams (around 2012), I found myself of the receiving end of a few of such calls and then ended up researching this kind of scam and the (fake) companies behind them, getting a good understanding of how and why such scams work. A regularly cited paper on the subject, written together with three others, was presented at Virus Bulletin 2012. I also shared my research with other researchers, the FTC and law enforcement.